Cloud Infrastructure and Entitlements Management (CIEM)
Your Cloud Identities. De-risked
Gain complete visibility and control over cloud permissions to minimize risk and enforce least privilege at scale
De-risk your cloud with CIEM - an integral part of Qualys TotalCloud™ - an Al-powered CNAPP solution
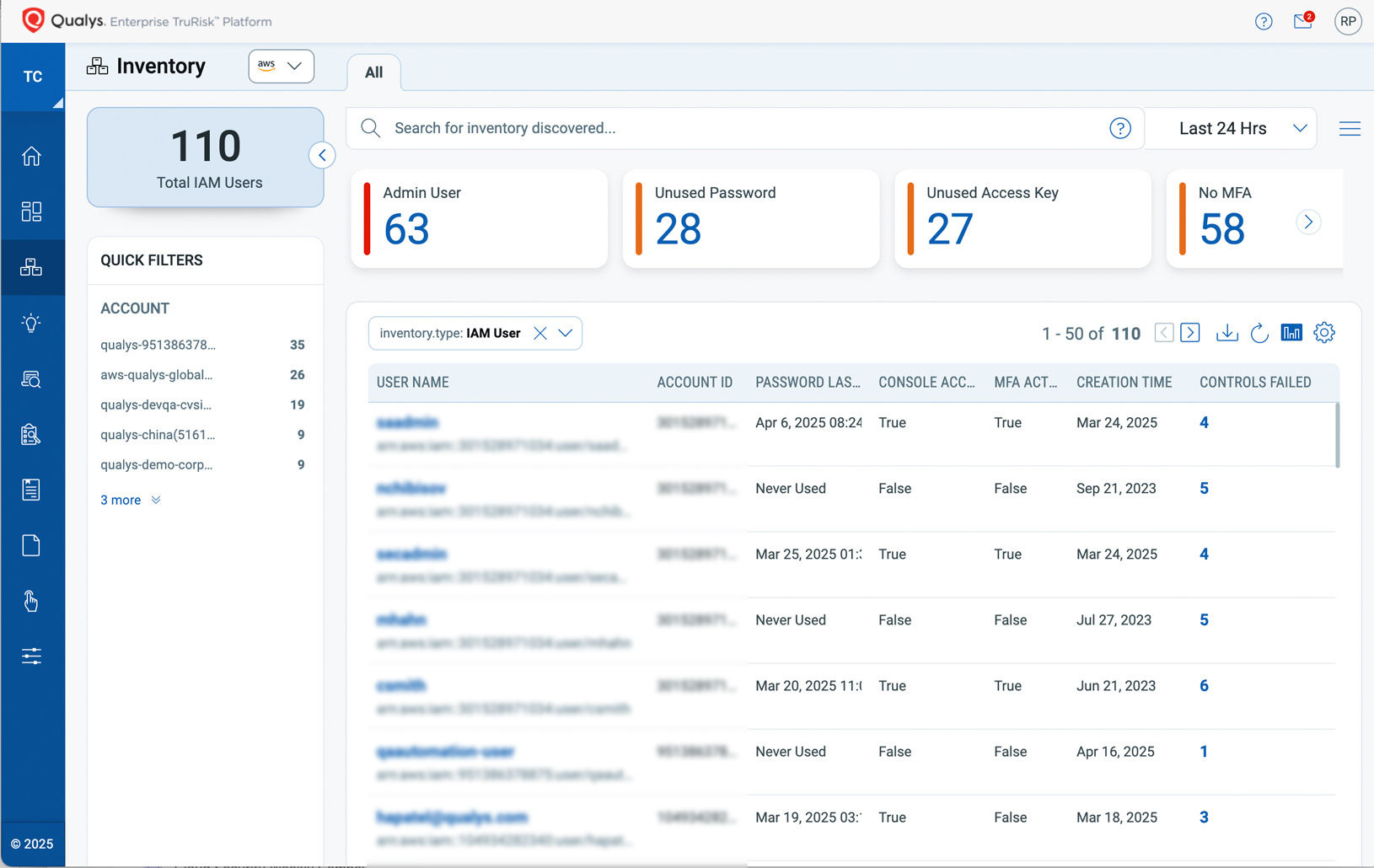
Discover Identities and Permissions
Discover and inventory users, roles, and other cloud entitlements to gain a complete understanding of your identity landscape.
Identify and track permissions and entitlements across your environment, reducing the risk of excessive access.

Prioritize with TruRisk Insights
Leverage TruRisk Insights to identify and prioritize potential security risks based on their potential impact.
Identify the resources impacted by a potential security threat, enabling targeted response and remediation.
Analyze potential lateral movements to understand the scope of a security threat and prioritize response efforts accordingly.

Remediate to Reduce Risk
Minimize the risk associated with overly permissive identities by reducing unnecessary permissions.
Utilize automation workflows to scale response and remediation efforts, ensuring timely and consistent risk reduction.
Leverage automation to remediate permissions and reduce risk across your environment, improving overall security posture.

Assess and Monitor
Continuously monitor overly permissive entitlements and unused identities to identify potential security risks.
Track new identities, permissions, and events from cloud providers in real-time, enabling prompt detection and response to security threats.

Continuous visibility, control, and automated least-privilege access for every identity across your cloud environments
Detect Risky identities and access privileges across multi-cloud environments, providing visibility, control, and enforcement of least-privilege access.

Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.